
Security is always excessive until it’s not enough
–Robbie Sinclair, Head of Security, Country Energy, NSW Australia
According to a study in Analytics service source, approximately 1500 iPhone and iPad applications currently available in the App store contain a bug that breaks HTTPS.
iPhone analysts have also identified an out-of-date version of open source code library AF networking as the source of the vulnerability. The library itself is already patched; however, there are thousands of apps that still use the old insecure version.
Researchers Simon Bovi and Mauro Gentile wrote on their paper that even though the apps were tested on a real device, unexpectedly, it was found that all the SSL traffic could be intercepted on a regular basis through a proxy like Burp without any kind of intervention.

All of these findings evoke me to think that there is only one side of the equation, the iOS side. Is iOS no more secure?
Well, of course, iOS is undoubtedly easy to use and has always been an operating system that has authoritatively been proven to be impossible or at least hard to hack. The staggering number of users have convinced the iPhone developers to come up with all the attractive latest iOS trends now. Along with these stats, let me tell you something else. During my in-depth research on iOS security, I found something bizarre.
Did you know that iOS was certified to be the hardest operating system to hack by the FBI?
The agency then testified to US Congress that they could not hack iOS, so they requested the government to force Apple to install a backdoor into their operating system. Fortunately, Congress stood with Apple, and they say the FBI never asked for any help again.
But that’s old news. Today, even an amateur tech person can jailbreak an iPhone and its applications. This backstreet practice of jailbreaking iPhones gives them more control of the operating system. Even you can customize your system and modify pre-installed applications and integrate other apps apart from the App store with little hacks and tricks. So I believe the answer to my prior Question,
“Is iOS no more secure?” is
No. It’s Not.
iOS Security: The Threat
Application security is no longer an afterthought. Unsecured applications across various platforms pose massive security threats since hackers and cybercriminals always find a way to bypass defences. Looking at the evolving number of organizations developing their own applications and integrating them with open source code results in significantly increased risks. Therefore, security testing in applications is critical, especially in iOS.
Currently, iOS app development is huge in demand because of its high revenue-generating system. iOS devices require less learning curve due to highly similar functions, and on top of that, they are faster, smoother and reliable. However, we see many iOS applications lack security of the sensitive user or business data.
Most of the information is stored in the app without the encryption format. This can lead to data sharing to third party apps which are risking your private information on several levels. So if your business application is built on iOS or by any chance, you plan to create your web presence with custom iOS development, it’s time you turn a little vigilant towards safety.
That’s why I decided to discuss the much needed iOS application security practices and measures that can save your business from an immense cyber incident.
These safety operations will cover how to secure the stored data or sending or receiving data over a network. So let us start talking about some of the simplest methods to manage iOS application security issues.
Here we will primarily focus on three significant factors:
- Storing your user data safely
- Using Apple’s new cryptographic APIs.
- Securing data transportation
For Storing Your User Data
If you follow the iOS app development process, you will notice OS already provides certain security features. Almost all the devices with an A7 processor, contain a coprocessor known as Secure Enclave that powers the security features in a hardware-accelerated format.
-
Apple’s App Sandbox:
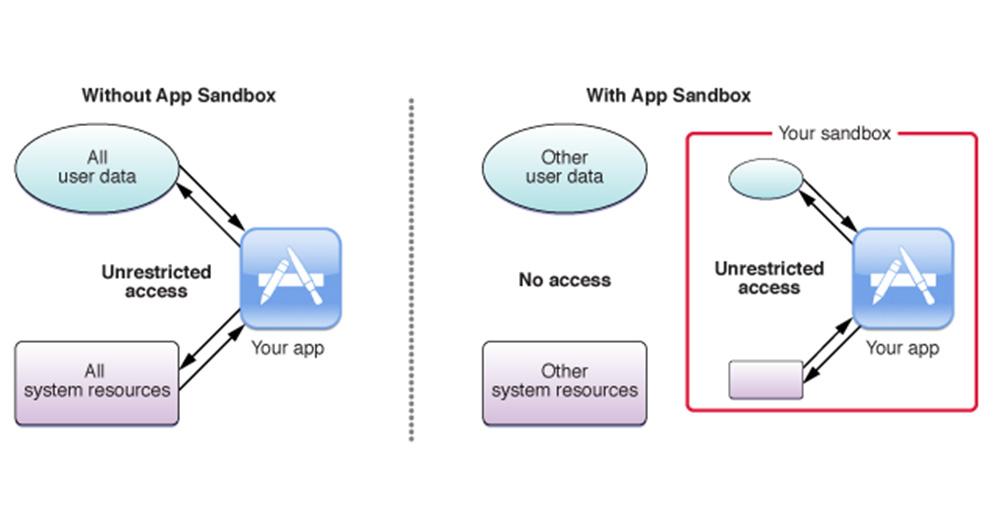
All apps that run on iOS work in a sandbox to ensure that the app can only store the data stored in Apple’s unique directory. In case, any app wants to access the data outside of the home directory; it will have to use services provided by iOS. This way, no other app can modify or access the data from your application.
Similarly, Apple’s app Sandbox is charged by UNIX’s user permissions and confirms that the apps get executed with a less privileged mobile user. Everything that comes outside the app’s home directory automatically becomes Read-only.
Moreover, for any specific operation, an application needs to declare certain entitlements. These entitlements get signed together with the app and cannot be changed. Some entitlements are even limited to be used if Apple permits them. For instance, services like CarPlay. They need special permission as misusing them can cause fatal consequences.
Apart from this, for safe storage in your app, iOS has methods to prevent memory-related security bugs. You can issue Address Space Layout Randomization (ASLR) to randomize your assigned memory regions for every app on every startup. Or seek ARMs Execute Never (XN) feature to restrict malicious code from being executed.
-
Data Protection API:
You will find a Data Protection feature in every iOS app since iOS 4, allowing you to encrypt and decrypt the stored files in the directory. These processes are automatic and hardware-accelerated. This feature enables by default and can be configured on a per-file basis to increase security. Every file can use one of the four protection levels.
Here are the four protection levels:
No Protection
The file is not encrypted and accessible to all.
Complete until First user authentication
This is a default level that decrypts the file after the user unlocks their device for the first time. The file stays decrypted until they reboot the device.
Complete unless open
The file is encrypted until started for the first time, and stays alive even when the device gets locked by the user.
Complete
The file can only be accessed when the device is unlocked.
You can specify the protection level when you create files but make sure it fits your needs. If your system has files with supreme data, I will suggest going for the highest protection level possible.
-
Keychain :
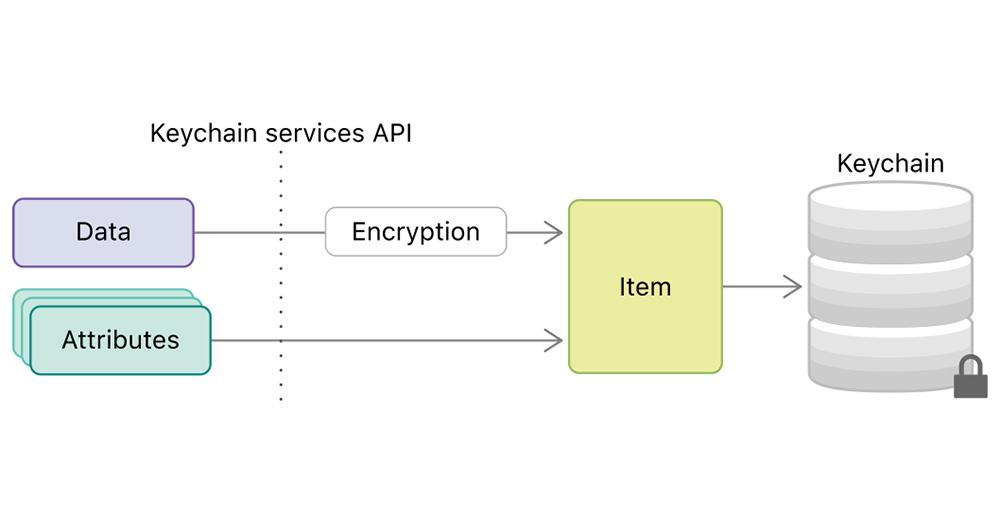
The Keychain is a safe place to store small data chunks. The iOS system generally uses this to store data like passwords and certificates, and only the developer will have access to this data storage.
Your business application or app group will have its own space in the Keychain. You can define access policies for authentication and accessibility. This will require user presence (Face ID or Touch unlock) for this. Additionally, the iOS keychain also gives you the power to decide between the local storage and the iCloud synchronized to all your Apple devices.
Now, merely securing data is not sufficient for a secure system environment. Let’s also look at securing your data transportation on a network which is again an essential phenomenon for the business.
For Securing Data Transportation:
After securing your user data, it is crucial to proceed towards securing the communication between your app and its remote counterparts. Since network hacking is the most common cybercrime, a safe data transport will prevent hackers from collecting private data by sniffing the network traffic or running harmful servers.
Here are few measures for a safe data transit :
-
HTTPS
Most of the network communication is performed over the HTTP protocol between the server and the client. Although you must notice, HTTP connections are not encrypted by default. It is effortless for attackers to turn a middle man from your local network.
With iOS 9, Apple introduced a new feature called App Transport Security (ATS) which improves the network communication security in your business app. All insecure connections are blocked by default in ATS and are secured with TLS.
aLSO, if your application contains an in-app browser, try using NSAllowsArbitaryLoadsInWebContent configuration that will allow your users to browse normally and still maintain the highest security solutions.
-
SSL Pinning
With HTTP connections, the system verifies everything automatically. It analyses the server certificate and checks its validity for the domain. This ensures that the connected server is not harmful.
However, looking at how advanced cyber crimes have turned, there is always a way for the attacker to reach you. If I were a hacker, to circumvent this mechanism, I would be required to explicitly trust another certificate in the user’s device setting or compromise a certificate authority. Furthermore, it will not be tough to perform an attack to read all your messages between the client and the server.
Do not worry; I chose not to get into hacking. Despite such attacks, you can secure your app through SSL or Certificate Pinning. You can implement SSL with a list of valid certificates, in your app bundle. Therefore, your app can check whether the certificate used by the server is on the list or not. If yes, only then it can communicate with the server.
-
CloudKit:
All the practices mentioned above would require a server for implementation. But If your app does not need a server, you can use Apple’s CloudKit. This permits you to store your data on iCloud containers while using Apple’s ID as a login system for your app.
When I suggest CloudKit, you can rely on this since it is an expert proven measure. CloudKit was created with security in mind. The cherry on the cake here is that the entire process is hassle-free. All the communication between the server and your app is done using Apple’s client-side CloudKit framework.
Also, If you have additional web or Android apps, you can still use CloudKit via Web and Javascript services.
The excellent news is CloudKit is free of charge up to a certain amount. So you can reach your audience without fearing the cost of traffic, requests or data storage.
-
End-to-end encryption:
We cannot talk about secure data transit and miss out end-to-end encryption. This feature is literally the holy grail for secure data transport. I will encrypt your messages in a format that only the sender and the receiver can decrypt them and neither your servers nor Apple itself can read the exact text data.
Nonetheless, end-to-end encryption is not easy to implement and needs heavy cryptographic experience. But you always have the option to consult a third-party expert to help you with the encryption mechanism.
For Cryptographic APIs
Cryptography is hard to get right. It is generally a sensible idea to rely on proven crypto processes rather than reimplementing them yourself. Apple’s Cryptokit is a new API that came along with iOS 13, to perform and implement security protocols.
CryptoKit enables you to use the SecureEnclave, to get safe functions cryptographically that can also be optimized for its hardware.
However, If you support older iOS versions, you have the option of using low-level APIs or open-source third party libraries such as CryptoSwift.
-
Data Hashing
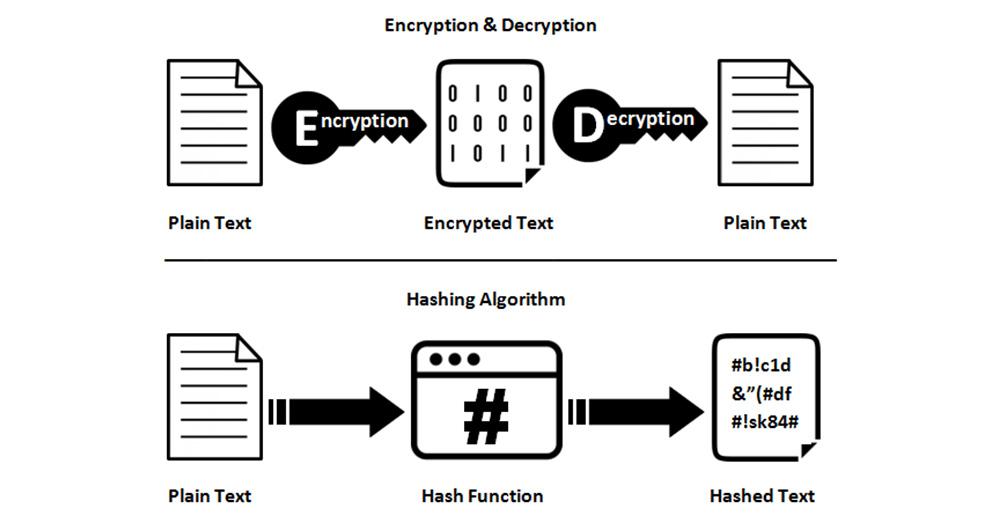
This term might sound illegal, but Hash functions are those that convert arbitrary size data values to fixed-sized values. A good Hash function will minimize the duplication of the output values and be very fast to commute. With CryptoKit, you can easily implement data hashing. All you need to do is call the hash function and choose the Hash algorithm.
In any scenario, you feel the process getting heavy for you, always seek an expert.
-
Data Authentication using Message authentication codes
A MAC ( Message Authentication Code) is used to authenticate the sender of the message to confirm its integrity. This way, the receiver can also verify the origin of the message and detect changes.
To use this kind of integrity checks, there are various mediums. For instance, you can use Cryptoswift’s hashed authentication codes, also known as HMACs. This is a very generic type that can be applied with all the Hash functions in CryptoSwift.
-
Encrypting data using Symmetric keys:
Data encryption and decryption using symmetric keys are simple too. You will have two available ciphers there: ChaChaPoly or AES-GCM.
I can give you a brief glance at it but make sure not to hardcode these symmetric keys in your app. What you can do is generate a symmetric key at runtime, and then securely store it in your Keychain. That way, no one will have access to your key to data decryption.
-
Creating and Verifying Signatures:
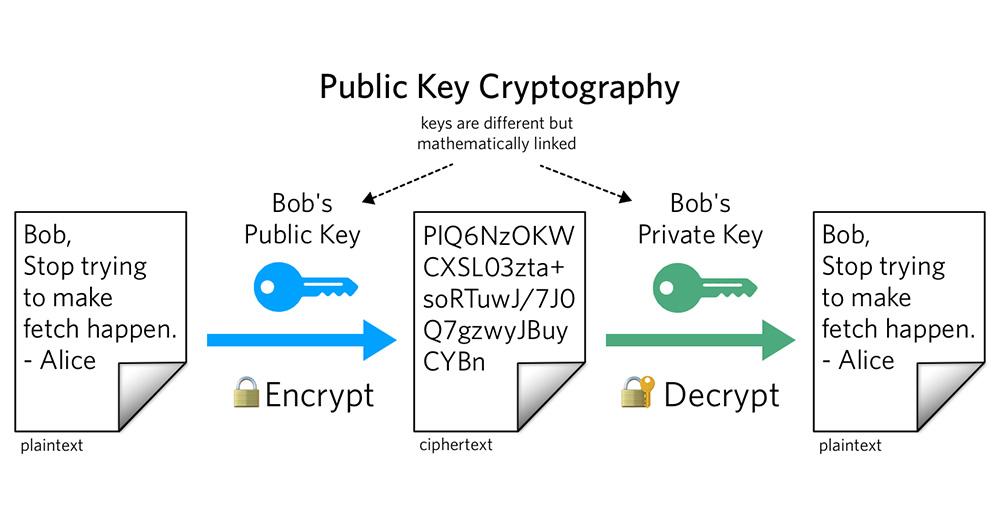
If you want to send messages to your client with credibility, the most straightforward alternative is to use signatures. To do so, you will need a public and private key pair. Any data can be signed using the private key.
The signature, along with the actual data, will be further sent to the receiver who can use the public key to verify your signature.
All the security parameters mentioned above mark the exceptional future of iOS app development in the mobile app development industry. One should know that iOS apps with the property safety measures can be a treasure.
Wrapping Up
I must agree that creating robust and dynamic business iOS applications is not an easy task. But you can always make the best out of your apps by following these security practices. For an enterprise, protecting the user, data must be a priority and should never be ignored. iOS app development requires following the strict guidelines of Apple’s security system. You can find even more information on Apple’s security guide that technically depicts how data is secured in iOS. Let’s make our applications safe and secure enough to protect them from any attack that harms our business.







Great and informative article.Thank you so much.
This is my first visit here. Out of the many comments on your articles, I think I’m not the only one amusing myself here.
Thanks for sharing such useful information with us. This blog really help me. Keep sharing
Nice and helpful information shared by this article with us and I hope that we will also get more new information regarding this post as soon as.